Security researchers have discovered billions of exposed records online, calling it the “mother of all breaches”.
However, the dataset doesn’t seem to be from one single data breach, but more a compilation of multiple breaches. These sets are often created by data enrichment companies. Data enrichment is the process of combining first party data from internal sources with disparate data from other internal systems or third party data from external sources. Enriched data is a valuable asset for any organization because it becomes more useful and insightful.
The researchers stated:
“While the team identified over 26 billion records, duplicates are also highly likely. However, the leaked data contains far more information than just credentials – most of the exposed data is sensitive and, therefore, valuable for malicious actors.”
In other news about leaked personal data, a cybercriminal going by the name of “emo” claims they have 15 million unique records of project management tool Trello accounts for sale.

Trello is used by many organizations, so it understandably raised some concerns.
Atlassian, the company that runs Trello, however denies there has been a breach. It seems as if someone has used a large collection of email addresses and tested it against Trello.
This brings us to the question: when do you call a giant leak of personal information a breach, and when don’t you?
A definition of a breach that makes sense to me is this one:
“A breach is an incident where data is inadvertently exposed in a vulnerable system, usually due to insufficient access controls or security weaknesses in the software.”
So you might say that exposing of billions of records was a breach because it is unlikely the instance was left open on purpose. After all, that amount of data can be sold for a pretty penny.
And Atlassian can safely say it was not breached, since the criminals used an existing feature. Maybe in larger numbers than intended, but why admit you shouldn’t have allowed it?
Some people will say that a data breach can only be the result of a hack and everything else is a leak. If you look at it that way, neither one of the datasets came from a breach. One set was stumbled upon and the other was created by using a legitimate API.
But to those affected the end result is pretty much the same whether your data was leaked in a breach, accumulated by scraping, or gathered by a data enrichment company. Your information is out there in the open for every cybercriminal to use at their perusal.
If you want to find out if your data is exposed online, you can try our free Digital Footprint scan. Fill in the email address you’re curious about (it’s best to submit the one you most frequently use) and we’ll send you a report.
You might be surprised. Remember though that it’s not embarrassing to you if your email address was found in a breach, but it is good to know if it was and where a password may have been included.
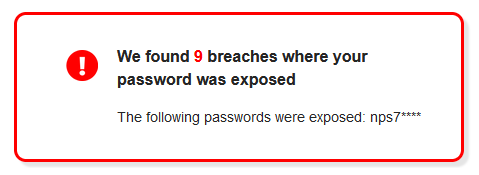
If the passwords it throws up at you look familiar, it would be a good idea to change the password where you’ve used it, enable 2FA, and check if it’s been re-used for other accounts.
Scammers are very good at using information found in breaches in social engineering attacks. Even the fact that your data may have been leaked in a breach is something scammers will readily use to launch a phishing attack and see what more they can find out from you.
Last year, over 2,000 companies and government entities reported data breaches impacting over 400 million personal accounts. Set up Identity Monitoring to get alerts whenever your data is exposed in a new breach.
Update January 26, 2024
The source of the dataset has been identified as data breach search engine Leak-Lookup.
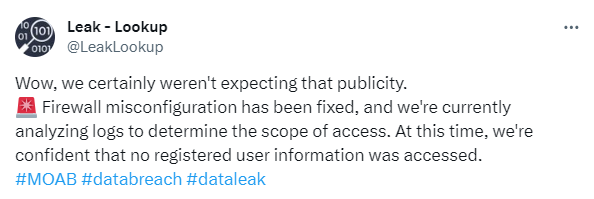
Leak-Lookup says the initial access was gained sometime around the start of December, due to a misconfigured server. Our point remains the same. The existence of data aggregation services, whichever service they may provide, does increase the risk of exposure, so it comes with great responsibility for those that set it up.











